 |
| May 07, 2019 | Volume 15 Issue 17 |
Software News & Products
Designfax weekly eMagazine
Archives
Partners
Manufacturing Center
Product Spotlight
Modern Applications News
Metalworking Ideas For
Today's Job Shops
Tooling and Production
Strategies for large
metalworking plants
hyperMILL 2024 CAD/CAM software suite
 OPEN MIND Technologies has introduced its latest hyperMILL 2024 CAD/CAM software suite, which includes a range of powerful enhancements to its core toolpath capabilities, as well as new functionality for increased NC programming efficiency in applications ranging from 2.5D machining to 5-axis milling. New and enhanced capabilities include: Optimized Deep Hole Drilling, a new algorithm for 3- and 5-axis Rest Machining, an enhanced path layout for the 3D Plane Machining cycle, better error detection, and much more.
OPEN MIND Technologies has introduced its latest hyperMILL 2024 CAD/CAM software suite, which includes a range of powerful enhancements to its core toolpath capabilities, as well as new functionality for increased NC programming efficiency in applications ranging from 2.5D machining to 5-axis milling. New and enhanced capabilities include: Optimized Deep Hole Drilling, a new algorithm for 3- and 5-axis Rest Machining, an enhanced path layout for the 3D Plane Machining cycle, better error detection, and much more.
Learn more.
Find test data issues faster: AI Anomaly Detector
 It can take months of manual engineering time to detect test data abnormalities. Now the task can be performed in a flash. Artificial intelligence software provider Monolith has developed the industry's first AI-powered Anomaly Detector software that can discover a broad range of issues in test data fast -- measurement or sensor errors, user errors, system malfunctions, or incorrect usage of the system during testing. It does this by automating the process of raw test data inspection to look for potential errors or abnormalities across hundreds of test channels.
It can take months of manual engineering time to detect test data abnormalities. Now the task can be performed in a flash. Artificial intelligence software provider Monolith has developed the industry's first AI-powered Anomaly Detector software that can discover a broad range of issues in test data fast -- measurement or sensor errors, user errors, system malfunctions, or incorrect usage of the system during testing. It does this by automating the process of raw test data inspection to look for potential errors or abnormalities across hundreds of test channels.
Learn more.
Loss-free conversion of 3D/CAD data
 CT CoreTech-nologie has further developed its state-of-the-art CAD converter 3D_Evolution and is now introducing native interfaces for reading Solidedge and writing Nx and Solidworks files. It supports a wide range of formats such as Catia, Nx, Creo, Solidworks, Solidedge, Inventor, Step, and Jt, facilitating smooth interoperability between different systems and collaboration for engineers and designers in development environments with different CAD systems.
CT CoreTech-nologie has further developed its state-of-the-art CAD converter 3D_Evolution and is now introducing native interfaces for reading Solidedge and writing Nx and Solidworks files. It supports a wide range of formats such as Catia, Nx, Creo, Solidworks, Solidedge, Inventor, Step, and Jt, facilitating smooth interoperability between different systems and collaboration for engineers and designers in development environments with different CAD systems.
Learn more.
Top 5 reasons for solder joint failure
 Solder joint reliability is often a pain point in the design of an electronic system. According to Tyler Ferris at ANSYS, a wide variety of factors affect joint reliability, and any one of them can drastically reduce joint lifetime. Properly identifying and mitigating potential causes during the design and manufacturing process can prevent costly and difficult-to-solve problems later in a product lifecycle.
Solder joint reliability is often a pain point in the design of an electronic system. According to Tyler Ferris at ANSYS, a wide variety of factors affect joint reliability, and any one of them can drastically reduce joint lifetime. Properly identifying and mitigating potential causes during the design and manufacturing process can prevent costly and difficult-to-solve problems later in a product lifecycle.
Read this informative ANSYS blog.
How a BattleBot was built using Onshape
 Learn how RoboGym Robotics, a veteran BattleBots team, said goodbye to Solidworks and took their design game to the next level using Onshape, the cloud-native, all-in-one CAD and PDM solution. RoboGym was able to analyze key components of their Roundhouse BattleBot like its armor and weapon bar, run simulations, collaborate, iterate, and optimize their design to its fullest.
Learn how RoboGym Robotics, a veteran BattleBots team, said goodbye to Solidworks and took their design game to the next level using Onshape, the cloud-native, all-in-one CAD and PDM solution. RoboGym was able to analyze key components of their Roundhouse BattleBot like its armor and weapon bar, run simulations, collaborate, iterate, and optimize their design to its fullest.
Read this informative Onshape blog.
Trick to measuring angles in SOLIDWORKS
 Learn from the pros at TriMech how to take angle measurements easily in SOLID-WORKS. TriMech has an entire YouTube channel dedicated to SOLIDWORKS tips, and the company is excellent at training too.
Learn from the pros at TriMech how to take angle measurements easily in SOLID-WORKS. TriMech has an entire YouTube channel dedicated to SOLIDWORKS tips, and the company is excellent at training too.
View the video.
COMSOL Multiphysics Version 6.2 is here
 COMSOL Multiphysics Version 6.2 introduces faster solvers for turbulent fluid flow, electric motors, and room acoustics. It also brings data-driven surrogate model functionality for creating multiphysics-based digital twins and building fast and accurate standalone simulation apps. Get the full details of what's new in the latest version.
COMSOL Multiphysics Version 6.2 introduces faster solvers for turbulent fluid flow, electric motors, and room acoustics. It also brings data-driven surrogate model functionality for creating multiphysics-based digital twins and building fast and accurate standalone simulation apps. Get the full details of what's new in the latest version.
Learn more.
17 ways SOLIDWORKS 2024 helps you work faster
 SOLIDWORKS 2024 helps designers and engineers work faster than ever. Learn all about improvements to core 3D CAD modeling features, new 3D modeling techniques, and graphical and software performance boosts that will help you get your parts made and your products developed in record time.
SOLIDWORKS 2024 helps designers and engineers work faster than ever. Learn all about improvements to core 3D CAD modeling features, new 3D modeling techniques, and graphical and software performance boosts that will help you get your parts made and your products developed in record time.
View the video.
6 tips to streamline workflow in Mastercam 2024
 Mastercam 2024 CAD/CAM software has been intentionally upgraded to make programming fast and easy. It prioritizes streamlining workflow so that the entire machining process -- from design to QC -- is as efficient as possible. Learn how to maximize the benefits of Mastercam 2024, including special toolpaths, easier hole-making operations, wireframe shortcuts, and more.
Mastercam 2024 CAD/CAM software has been intentionally upgraded to make programming fast and easy. It prioritizes streamlining workflow so that the entire machining process -- from design to QC -- is as efficient as possible. Learn how to maximize the benefits of Mastercam 2024, including special toolpaths, easier hole-making operations, wireframe shortcuts, and more.
Read this informative Mastercam blog.
How CT data analysis is helping TE Connectivity reach their goal of end-to-end quality inspection
 In a bid to cut their mold and part development process to 25% of the time it took in the past, TE Connectivity has taken ambitious steps to interconnect design and simulation with quality measurement. Learn how the company, in collaboration with PTC (Creo) and Volume Graphics, has worked to ensure as-designed parts match as-manufactured parts as early in the process as possible. An in-depth and illuminating read.
In a bid to cut their mold and part development process to 25% of the time it took in the past, TE Connectivity has taken ambitious steps to interconnect design and simulation with quality measurement. Learn how the company, in collaboration with PTC (Creo) and Volume Graphics, has worked to ensure as-designed parts match as-manufactured parts as early in the process as possible. An in-depth and illuminating read.
Read the full article.
State-of-the-art mesh morphing technology for super optimization: Ansys and RBF Morph join forces
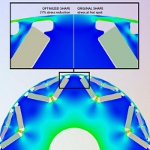 After a long and successful OEM partnership with Ansys, mesh morphing pioneer RBF Morph has two proprietary products featured among the world simulation leader's offerings: Ansys RBF Morph Fluids and Ansys RBF Morph Structures. Thanks to mesh morphing, companies can substantially reduce computational time while performing highly automated design optimization analysis, increasing products' reliability and performance while cutting costs, delivery time, and environmental impact.
After a long and successful OEM partnership with Ansys, mesh morphing pioneer RBF Morph has two proprietary products featured among the world simulation leader's offerings: Ansys RBF Morph Fluids and Ansys RBF Morph Structures. Thanks to mesh morphing, companies can substantially reduce computational time while performing highly automated design optimization analysis, increasing products' reliability and performance while cutting costs, delivery time, and environmental impact.
Read the full article.
Top Tech Tip: Creating drafts with the rib feature in Onshape
 Ribs are used to add stiffness and strength to parts without adding excessive weight or increasing wall thickness -- most commonly in molded parts that require a draft angle so the part can release from the mold. See the basics of how this is done in Onshape, which features the power of cloud computing, real-time collaboration tools, and a built-in PDM system -- all for the same price as CAD.
Ribs are used to add stiffness and strength to parts without adding excessive weight or increasing wall thickness -- most commonly in molded parts that require a draft angle so the part can release from the mold. See the basics of how this is done in Onshape, which features the power of cloud computing, real-time collaboration tools, and a built-in PDM system -- all for the same price as CAD.
Learn more.
How to design a spoon with subdivision modeling: SOLIDWORKS xShape
 Learn how to design a spoon with SOLIDWORKS xShape, which is found in 3D Sculptor on the 3DEXPERI-ENCE platform. xShape is a next-gen subdivision modeling tool that runs entirely in your browser and takes a freeform approach to creating complex shapes and surfaces. You can design 100% in the cloud or seamlessly integrate your xShape models with your SOLIDWORKS designs. Follow along with this 7-minute tutorial to see what it's all about.
Learn how to design a spoon with SOLIDWORKS xShape, which is found in 3D Sculptor on the 3DEXPERI-ENCE platform. xShape is a next-gen subdivision modeling tool that runs entirely in your browser and takes a freeform approach to creating complex shapes and surfaces. You can design 100% in the cloud or seamlessly integrate your xShape models with your SOLIDWORKS designs. Follow along with this 7-minute tutorial to see what it's all about.
View the video.
What's new in Onshape?
 Check out the latest updates to Onshape, the cloud-native product development platform that delivers professional-grade CAD capabilities with next-gen product data management. New features include customizable keyboard shortcuts, better BOM navigation, improved drawing tools, and new Learning Center content. With Onshape, users can innovate quickly while simultaneously or asynchronously collaborating with other stakeholders on any web-connected device.
Check out the latest updates to Onshape, the cloud-native product development platform that delivers professional-grade CAD capabilities with next-gen product data management. New features include customizable keyboard shortcuts, better BOM navigation, improved drawing tools, and new Learning Center content. With Onshape, users can innovate quickly while simultaneously or asynchronously collaborating with other stakeholders on any web-connected device.
View the video.
Open-access learning center for multiphysics modeling
 COMSOL, the developer of the COMSOL Multiphysics simulation software, has introduced a new online resource that provides no-cost, open access to modeling and simulation learning material across all areas of physics. Designed with the user in mind, the Learning Center offers a single entry point for users of all skill levels, where courses, articles, and videos present a clear path for learning how to use COMSOL Multiphysics for modeling and simulation.
COMSOL, the developer of the COMSOL Multiphysics simulation software, has introduced a new online resource that provides no-cost, open access to modeling and simulation learning material across all areas of physics. Designed with the user in mind, the Learning Center offers a single entry point for users of all skill levels, where courses, articles, and videos present a clear path for learning how to use COMSOL Multiphysics for modeling and simulation.
Check out the COMSOL Learning Center.
New app developed at Columbia University can secure all your saved emails
Easy Email Encryption, a new app in the making by researchers at Columbia University, encrypts all saved emails to prevent hacks and leaks, is easy to install and use, and works with popular email services such as Gmail, Yahoo, and more. [Credit: John S. Koh/Columbia Engineering]
While an empty email inbox is something many people strive for, most of us are not successful. And that means that we probably have stored away hundreds, even thousands, of emails that contain all kinds of personal information we would prefer to keep private.
Current defenses, such as Pretty Good Privacy (PGP) and Secure/Multipurpose Internet Mail Extensions (S/MIME), rely on public key cryptography that uses pairs of public and private keys generated by cryptographic algorithms. Because these systems are too technical and difficult for the average user, most people don't use them. As a result, many email accounts have been hacked, including such high-profile cases as the phishing attack on Hillary Clinton's top campaign advisor John Podesta and the 2016 email hack of one of Vladimir Putin's top aides.
In response to these kinds of widespread attacks, computer scientists at Columbia Engineering have built Easy Email Encryption (E3), an application for secure, encrypted email that is easy to manage -- even for non-technical users. Now in beta test mode, E3 automatically and invisibly encrypts email as soon as it is received on any trusted device, including smartphones, laptops, and tablets. It works on a variety of platforms including Android, Windows, Linux, and Google Chrome, and with popular mail services such as Gmail, Yahoo, AOL, and more.
The team, Professors Jason Nieh and Steve Bellovin and their PhD student John S. Koh, presented its study March 26 at EuroSys '19 in Dresden, Germany, one of the world's top forums focused on computer systems software research and development.
"Email privacy grows ever more critical as our email inboxes increase in size," says Koh, the paper's lead author. "Thanks to free and widely popular mail services like Gmail, users are keeping more and more emails, thus providing a one-stop shop for hackers who can compromise all of a user's emails with a single successful attack."
Ever since 1999, when the seminal "Why Johnny Can't Encrypt" paper showed how extraordinarily hard it was for people to send encrypted email, researchers have been trying to design encryption systems that are easier for the average user to manage. The problem is that they have stayed focused on end-to-end encryption solutions, where only the original sender and recipient can read the messages. Third-parties, including telecommunications and Internet providers, cannot eavesdrop as they cannot access the cryptographic keys to decrypt the conversation. While these solutions certainly work and offer the most security, PGP and S/MIME, the encryption solutions most favored by experts, are so complex that they are impractical, almost unusable, for a non-technical user.
"The field of email security is just begging for improvement," Koh notes. "For 20 years, the research community was fixated on end-to-end security. We took a different tack, positing that end-to-end encryption for email is not needed in the 21st century. Internet connections are increasingly protected by default using encryption. Our insight is that email needs to be protected when it's stored in our inboxes, not when it's being sent over the Internet, because hackers are mainly just trying to log into your email account. We thus apply an 'encrypt on receipt' model that provides excellent real-world security while being far more usable than end-to-end encryption."
Over the past three years, the Columbia Engineering team refined E3, trying many different approaches before finding a method that checked all the boxes they needed. They have been testing the app with a couple dozen study participants, many of whom were not particularly tech-savvy. All agreed that E3 is significantly easier to use than the state-of-the-art systems for secure email, to the point where E3 is almost as easy to use as a regular email client.
The team's new approach simplifies email encryption and improves its usability by implementing receiver-controlled encryption. Newly received messages are transparently downloaded and encrypted to a locally generated key, and the original message is then replaced. A major problem was how to handle multiple devices, especially important these days as most people read email on several devices. Rather than moving private keys around, which is hard to do securely and puts great demands on the user, the researchers used per-device key pairs. With this approach, only public keys need to be synchronized via a simple verification step. Hackers who successfully attack an email account or server can only gain access to encrypted emails. All emails encrypted prior to a breach are protected.
In E3, public keys are never shared with other people. They are self-generated and self-signed, and require no public key infrastructure for the user to understand. Previous work has shown that users find it confusing to correctly obtain and use public keys. In contrast, an E3 user needs only self-signed keys, and any public key exchanges among the user's devices are automated.
The researchers note that they do not intend E3 to be an end-to-end, maximum security solution, but rather a major improvement over the norm that is easy to deploy and use. Says Koh, "We traded perfection -- end-to-end, sender-controlled encryption -- for a significant increase in usability and the ability to protect what we now know is the real problem for most people."
The team is refining E3 and making its implementations -- the actual applications -- even easier to use by trying new approaches applicable to the modern user. They plan to make it available in the near future for Android users as an app freely available in the Google Play Store. An iOS version is also in the works.
The new research paper is called "Why Joanie Can Encrypt: Easy Email Encryption with Easy Key Management." It is available here.
Source: Columbia University
Published May 2019
Rate this article
View our terms of use and privacy policy
